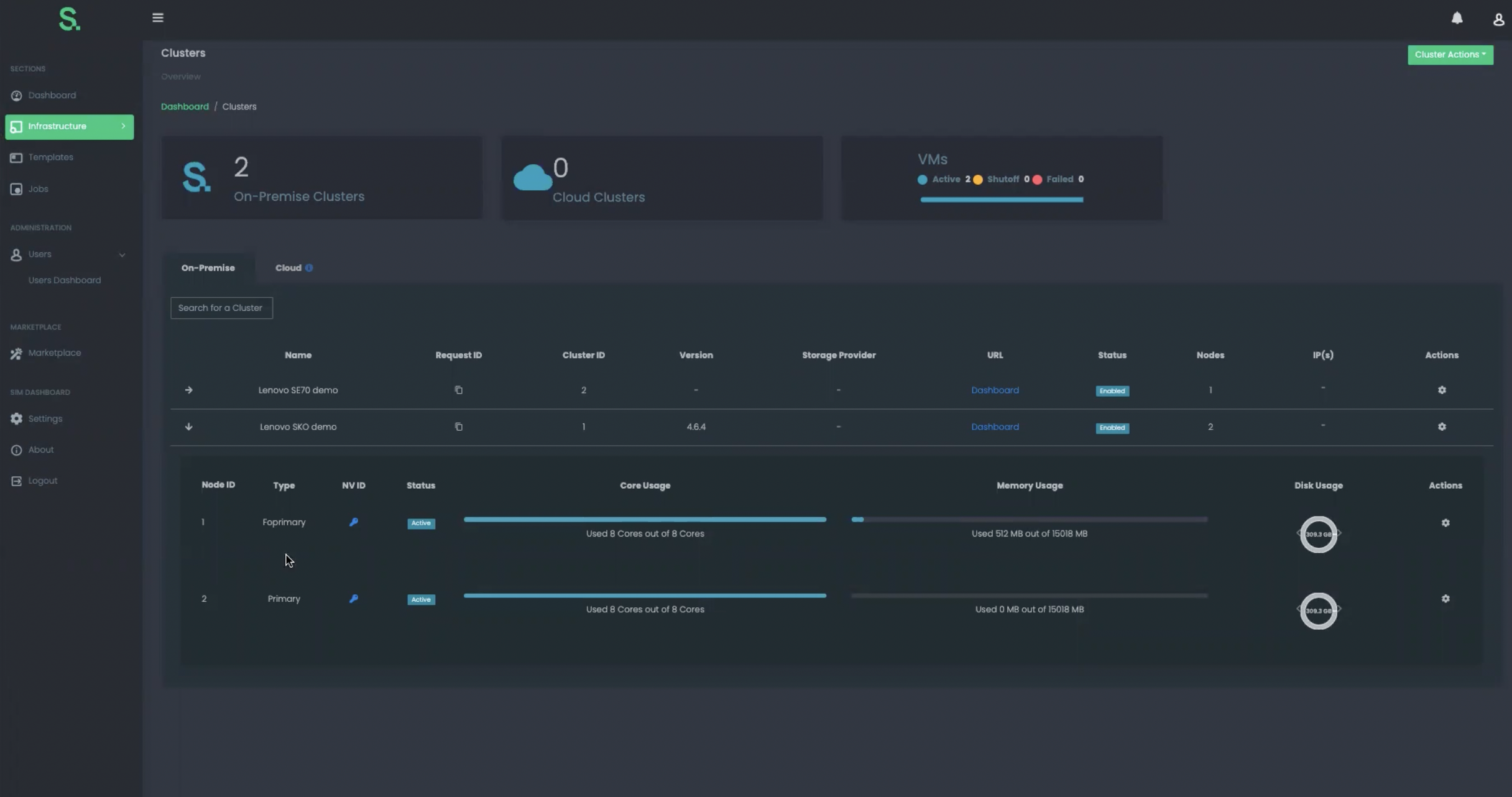
Sunlight is designed with security at its core. All components of the Sunlight stack are hardened. Thanks to Sunlight’s fine-grained CPU and memory allocation, it is possible to physically guard against CPU memory exploits. Control of IO interfaces allows you to separate content and network traffic so there is no sharing of physical drives or network physical interfaces.
Disaster Recovery
- Server, rack and availability zone-level HA policies
- Automated backup and fail-over processes
- Snapshot(s) hosted on redundant servers to ensure resilience and quick recovery from data loss
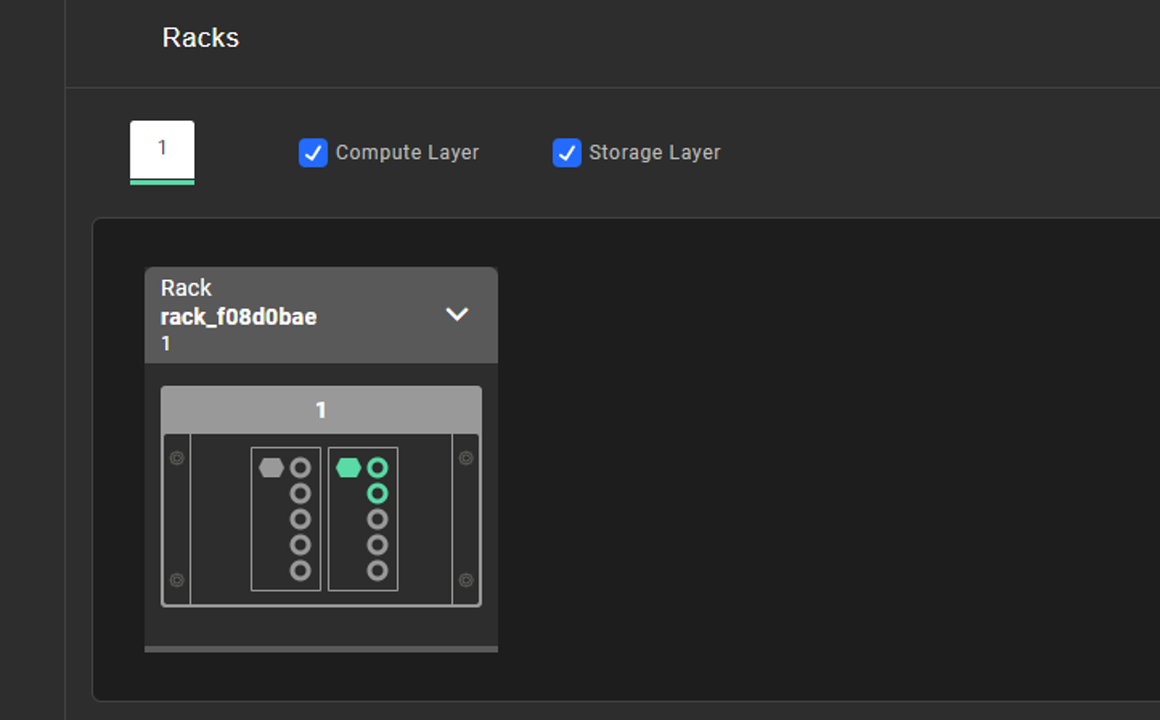
Data sovereignty
- Localize and store data in the location you choose.
- Data sovereignty is maintained at the site where it is captured or generated.
- Deploy locally, manage globally.
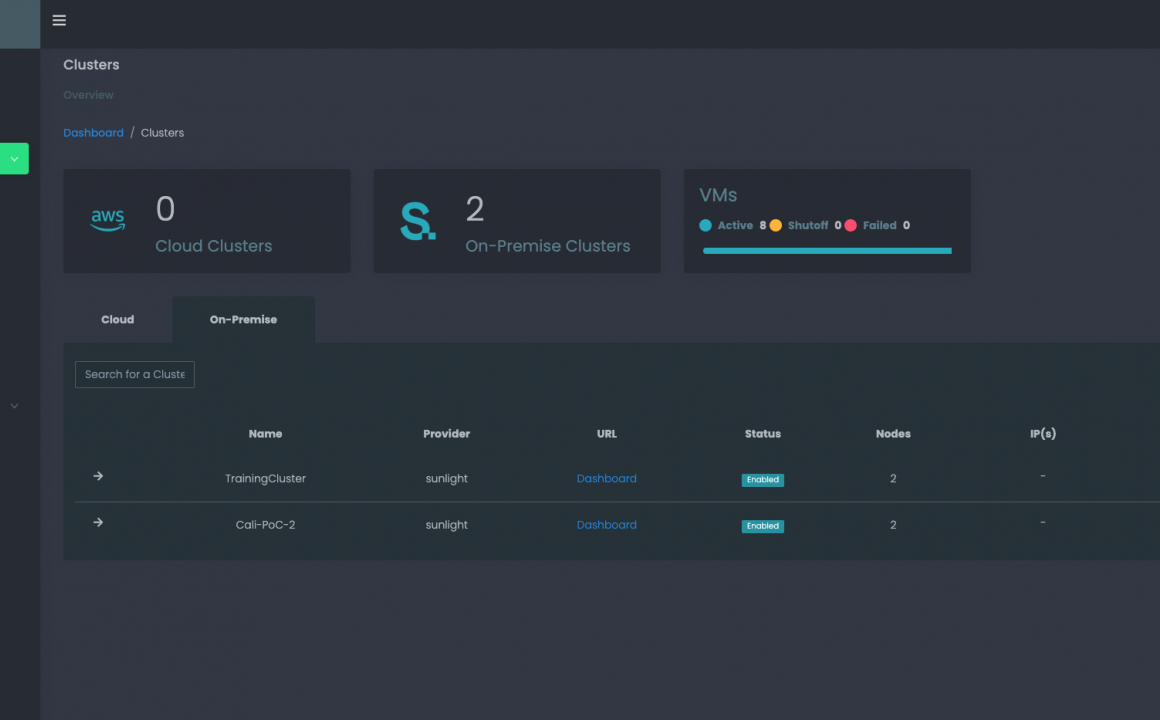
Disaster Recovery
- Server, rack & availability zone-level HA policies
- Automated backup and fail-over processes
- Snapshot(s) hosted on redundant servers to ensure resilience and quick recovery from data loss
AppLibrary for security applications
- Deploy applications (including cybersecurity applications) on demand with a single click.
- Choose a pre-built application or build your own.
Easy to implement and manage
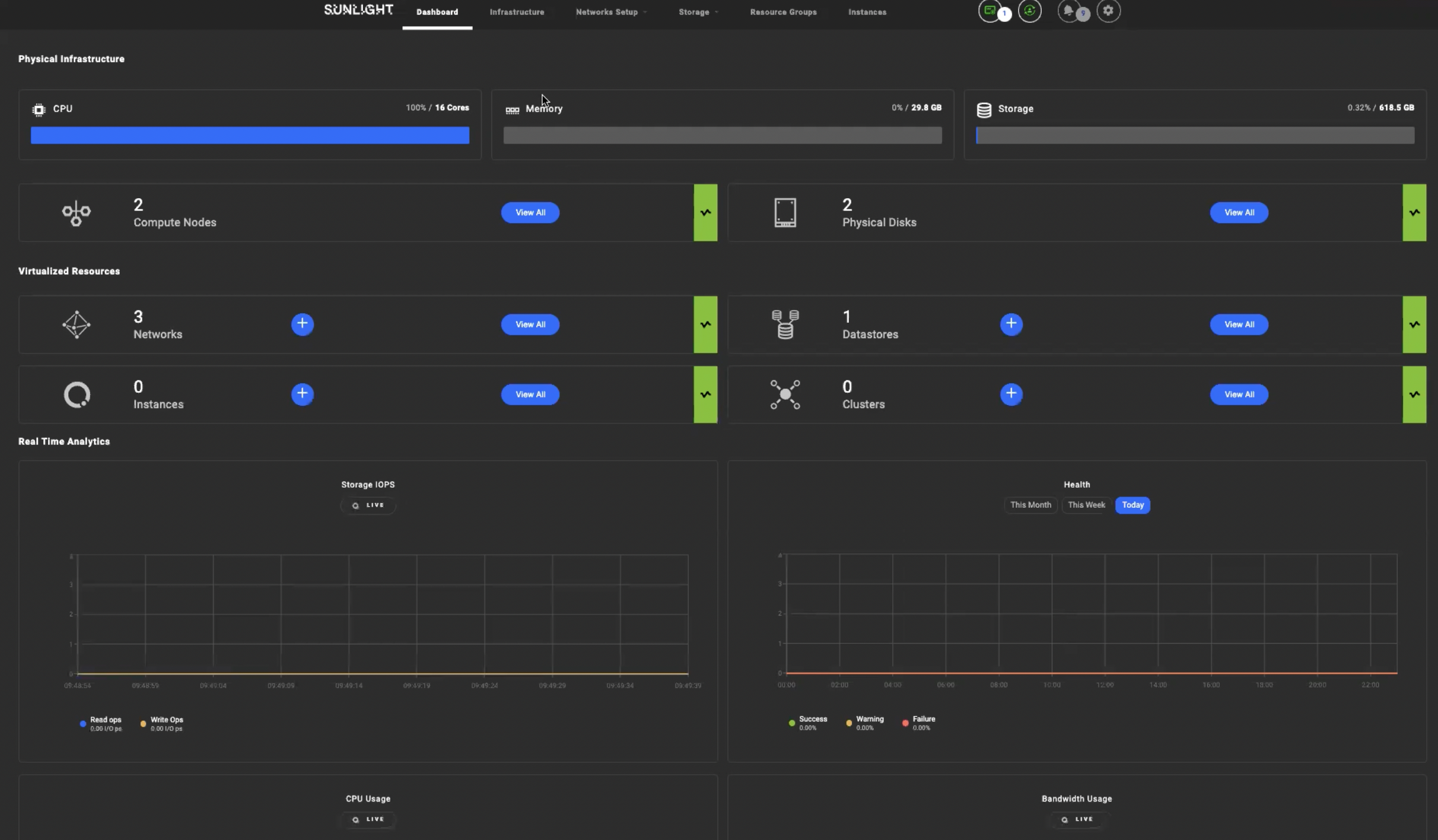
Sunlight HyperConverged Edge is easy to install - the complete Sunlight HCE stack can be installed on bare-metal servers in minutes. Sunlight is easy to manage - it includes the Edge Stack Console that allows you to manage all aspects of your Sunlight cluster, including fine-grained control of CPU, storage and network configuration and performance. The dashboard is installed as part of the HCE stack and is highly-available by design across the cluster.
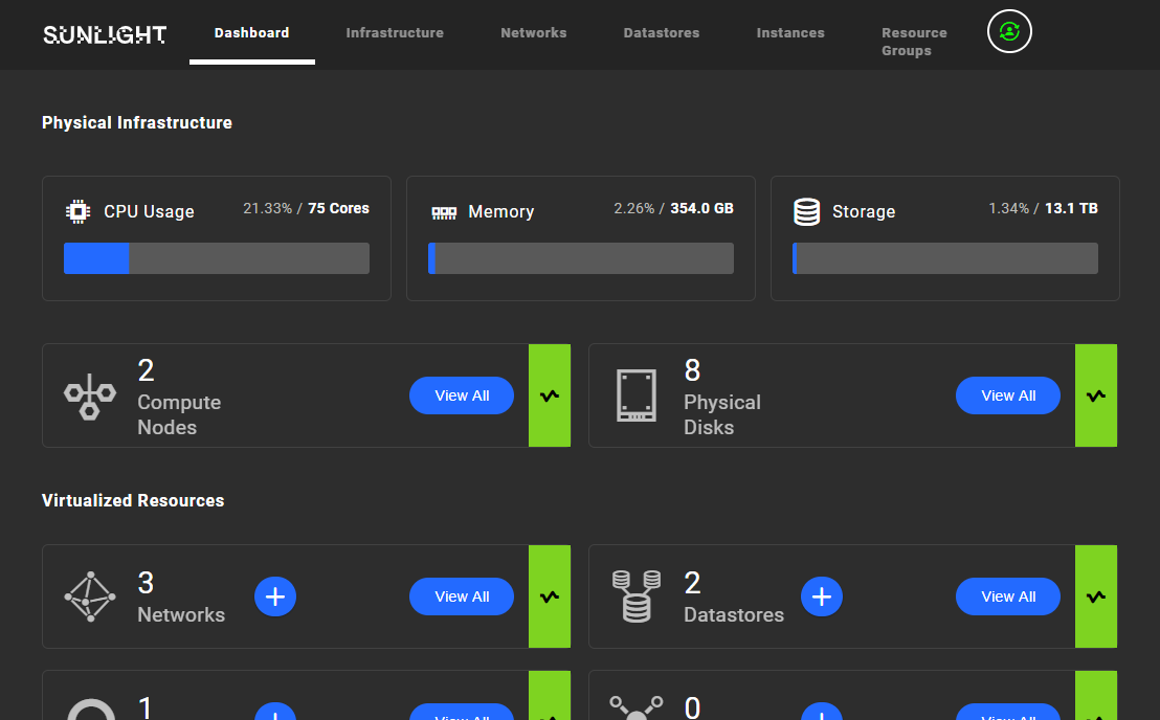
Highly Available
Sunlight is highly available, delivering fail-over and redundancy for mission-critical applications at the edge. Eliminate downtime and lower the cost of servicing remote locations by moving break-fix to regular business hours and with lower cost SLAs.
Secure
Sunlight is designed with security at its core. All components of the Sunlight stack are hardened. Thanks to Sunlight’s fine grained CPU and memory allocation it is possible to physically guard against CPU memory exploits. Control of IO interfaces allows you to separate content and network traffic so there is no sharing of physical drives or network physical interfaces.
Low Cost
Sunlight is priced for edge economics, with flexible terms on a per-node basis.